ASA Basics
ASDM
ASDM provides the GUI (Graphical user interface) to configure and manage the ASA. After enabling the ASDM we can use it in two different ways. 1. through accessing in browser. 2. through installing application on desktop. If we want to access through application then we can download it from ASA when first time accessing the ASDM through browser.
Enabling ASDM
- Check the ASDM bin file into flash (show disk0:) if is not present then upload it.
- After that tell to ASA which ASDM file will be use.
ASA1(config)# asdm image disk0:/asdm-731.bin - Enable the HTTP. By default it is disabled.
ASA1(config)# http server enable
hostname(config)# http server enable 443
NOTE: Port 443 is the default port for ASDM. If you want to change this port number then you can do it. If you are changing the port number for ASDM then you have to use this port number in your URL when you are accessing the ASDM. Example, if you change the port number to 444, Then enter the following: https://10.1.1.1:444 - Restrict the access (We should restrict the access. Here I have allowed the full subnet of /24 but in real environment you should use only particular IP addresses for the hosts, from which you want to access the ASDM)
ASA1(config)# http 192.168.1.0 255.255.255.0 INSIDE - Configure the username and password
ASA(config)#username cisco password cisco privilege 15 - Now we can access web page from browser or through ASDM-IDM Launcher application
https://192.168.1.254
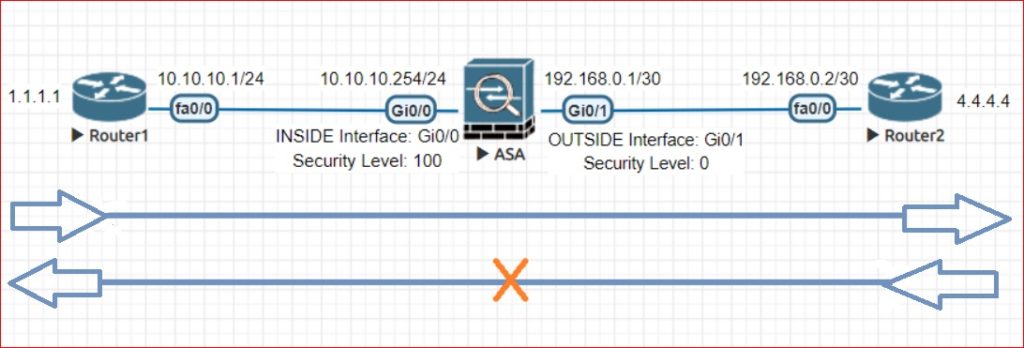
Security Level
Security level indicates how we trust an interface , comparing to other interfaces. A interface with high security level is more trusted then a interface which having lower security level. On ASA, we defines each interface with a security level and interface with security level acts like a zone.
By default, ASA not follow the zone concept. Zone is the concept of PALO ALTO and Checkpoint etc.
An interface with a high security level can access an interface with a low security level. But interface with low security level is not allowed to access an interface which is having high security level. If it is required then we can configure ACL for allow the traffic from low security level to higher security level.
But reverse traffic from lower security level to higher security level will be allow. Means, if we are sending a packet from INSIDE (Higher Security Level) to OUTSIDE (Lower Security Level) then reply packet will be allowed automatically. because ASA maintains session / connection table.
By default, Communication between two interfaces of same security level is also not allowed. If it is required then we can allow it using the command
ASA(config)#same-security-traffic permit inter-interface
NOTE: If you are one who is still confused with security level then you can understand it in the way of water flow. Water always can flow from higher place to lower place but it can’t flow from lower place to higher place and same is with ASA security levels.
If we we are giving the name INSIDE to a interface then security level will be set to 100 automatically and if we are giving the name OUTSIDE to a interface then security level will be set to 0 automatically. But we can change it if we want.
Security level can be set between 0 and 100.
Example: Below example is showing that traffic can move from higher security level to lower security level
INSIDE interface configuration
ASA1(config)# interface gi0/0
ASA1(config-if)# nameif INSIDE
INFO: Security level for “INSIDE” set to 100 by default.
ASA1(config-if)# ip address 10.10.10.254 255.255.255.0
ASA1(config-if)# no shutdown
Or
ASA1(config-if)# security-level 100
OUTSIDE interface configuration
ASA1(config)# interface gi0/1
ASA1(config-if)# nameif OUTSIDE
INFO: Security level for “OUTSIDE” set to 0 by default.
ASA1(config-if)# ip address 192.168.0.1 255.255.255.252
ASA1(config-if)# no shutdown
Or
ASA1(config-if)# security-level 0
NOTE: write erase command is used to erase the configuration. ASA doesn’t support erase startup-configuration command.
Factory Default
The factory default configuration is available only for routed firewall mode and single context mode.
ASA(config)# configure factory-default 192.168.1.1 255.255.255.0
Based on the management IP address and mask, the DHCP address
pool size is reduced to 253 from the platform limit 256
WARNING: The boot system configuration will be cleared.
The first image found in disk0:/ will be used to boot the
system on the next reload.
Verify there is a valid image on disk0:/ or the system will
not boot.
Begin to apply factory-default configuration:
Clear all configuration
Executing command: interface management0/0
Executing command: nameif management
INFO: Security level for “management” set to 0 by default.
Executing command: ip address 192.168.1.1 255.255.255.0
Executing command: security-level 100
Executing command: no shutdown
Executing command: exit
Executing command: http server enable
Executing command: http 192.168.1.0 255.255.255.0 management
Executing command: dhcpd address 192.168.1.2-192.168.1.254 management
Executing command: dhcpd enable management
Executing command: logging asdm informational
Factory-default configuration is completed
neural
Hi Avon, My apologies if you have faced any difficulties. We are just under construction face as well as we are looking for suggestions. so please feel free for share your feedback. It will be helpful for us.
Regards,
Admin
networkrare.com
i read most of blogs. great job
good but it will more helpful if you will share articles on new technologies
Hello my loved one! I want to say that this post is awesome,
great written and include approximately all vital infos.
Highly descriptive blog, I enjoyed that bit. Will there be a part 2?
please keep sharing on ASA. i know its now legacy but still in demand
Good work !
please also upload the post on sadwan
I have read this article and if I could I want to suggest you some attention-grabbing things or tips. Perhaps you can write subsequent articles relating to this article. I wish to learn more issues approximately it!
excellent
could you share the study material on BGP ?
You cover more useful information than I have seen elsewhere. Please could you share your sourceexperience with us?
Fantastic !
Hi,
I hope you are doing well.
I want to contribute a guest post article to your website that may interest your readers.