Cisco active standby failover feature provides the stateful failover , means if one firewall fails then traffic will be move on secondary firewall and users will not face any blimp in connectivity. For detailed overview on ASA active standby can read the below article.
ASA Failover Active/Standby (Failover and stateful link on different interfaces)
In below topology , we are using a single link for both failover link and stateful link. both firewalls are directly connected using a single linkon port Gi0/2. We can also connect both ASA firewalls through a layer 2 switch. but this switch should not have other connections as well as we should configure the VLANs on it. This is not compulsory but it is recommended by cisco due to security purpose.
We are having many things which should be in mind before configure the Active / Standby failover and after configure the failover. but we can’t cover all those things with this example. so we have already created a seprate articale for it.
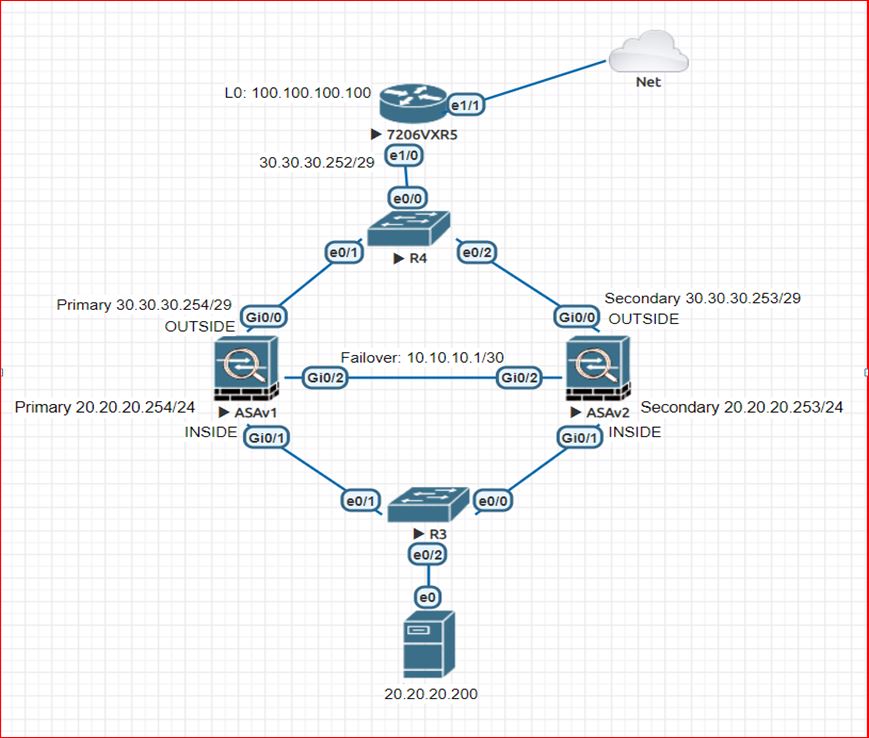
ASA1
Conf t
failover lan unit primary
failover lan interface FAIL_OVER GigabitEthernet0/2
failover link FAIL_OVER GigabitEthernet0/2
failover interface ip FAIL_OVER 10.10.10.1 255.255.255.252 standby 10.10.10.2
failover
int g0/2
no shut
interface GigabitEthernet0/0
nameif outside
security-level 0
ip address 30.30.30.254 255.255.255.248 standby 30.30.30.253
interface GigabitEthernet0/1
nameif inside
security-level 100
ip address 20.20.20.254 255.255.255.0 standby 20.20.20.253
wr
OPTIONAL
monitor-interface INSIDE
monitor-interface OUTSIDE
NOTE: The ASA requires something that can trigger the failover mechanism. By default all physical interfaces are monitored and used for trigger the failover as well as hardware and software failure is also triggers the failover. we can also define the monitoring of interfaces if we don’t want to monitor all the interfaces
ASA2
Conf t
failover lan unit secondary
failover lan interface FAIL_OVER GigabitEthernet0/2
failover link FAIL_OVER GigabitEthernet0/2
failover interface ip FAIL_OVER 10.10.10.1 255.255.255.252 standby 10.10.10.2
failover
int g0/2
no shut
ASA Failover Active/Standby (Failover and stateful link on different interfaces)
NOTE: This lab example is same as above one. just we added two extra highlighted commands
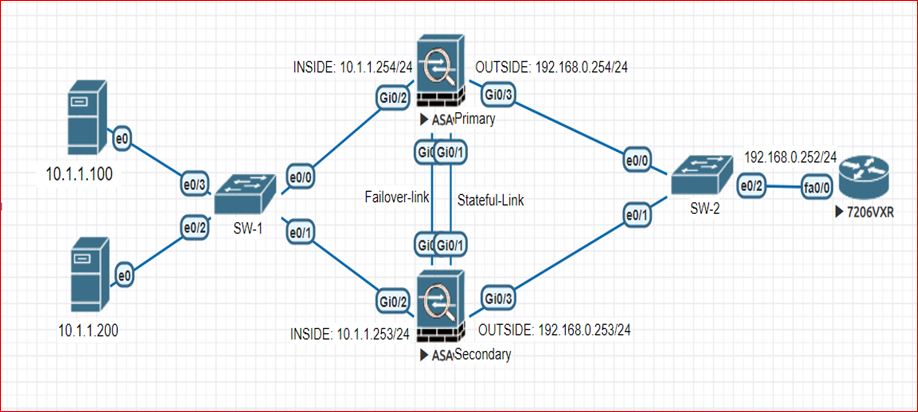
ASA1:
failover lan unit primary
failover lan interface FAILOVER GigabitEthernet0/0
failover interface ip FAILOVER 22.22.22.1 255.255.255.252 standby 22.22.22.2
failover link STATEFUL GigabitEthernet0/1
failover interface ip STATEFUL 11.11.11.1 255.255.255.0 standby 11.11.11.2
failover
int g0/0
no shut
int g0/1
no shut
interface GigabitEthernet0/2
nameif inside
security-level 100
ip address 10.1.1.254 255.255.255.0 standby 10.1.1.253
interface GigabitEthernet0/3
nameif outside
security-level 0
ip address 192.168.0.254 255.255.255.0 standby 192.168.0.253
ASA2:
failover lan unit secondary
failover lan interface FAILOVER GigabitEthernet0/0
failover interface ip FAILOVER 22.22.22.1 255.255.255.252 standby 22.22.22.2
failover link STATEFUL GigabitEthernet0/1
failover interface ip STATEFUL 11.11.11.1 255.255.255.0 standby 11.11.11.2
failover
int g0/0
no shut
int g0/1
no shut
Manual failover (when failover is not happening automatically or when required)
On active ASA:
ASA(config)# no failover active
Or
ASA(config)# failover active
On standby ASA:
Disabling the failover
hostname(config)# no failover
Restoring a Failed Unit
Below command is used for Restore a failed unit. Moving a failed unit to an unfailed state. it does not mean that ASA will be automatically move into active state. Restored ASA will still remain in the standby state until unless failover does’t trigger. But we can manually move it into actvie state if required.
hostname(config)# failover reset
Helpful Commands For Troubleshooting
ciscoasa# sh failover interface
interface FAIL_OVER GigabitEthernet0/2
System IP Address: 10.10.10.1 255.255.255.252
My IP Address : 10.10.10.2
Other IP Address : 10.10.10.1
ciscoasa# sh failover state
State Last Failure Reason Date/Time
This host – Secondary
Active None
Other host – Primary
Failed Ifc Failure 13:02:14 UTC Feb 9 2020
outside: Failed
====Configuration State===
Sync Done – STANDBY
====Communication State===
Mac set
ciscoasa# sh failover statistics
tx:8970
rx:8926
sh failover history
ciscoasa# sh failover interface
interface FAIL_OVER GigabitEthernet0/2
System IP Address: 10.10.10.1 255.255.255.252
My IP Address : 10.10.10.2
Other IP Address : 10.10.10.1
ciscoasa# sh failover descriptor
outside send: 00020000ffff0000 receive: 00020000ffff0000
inside send: 00020100ffff0000 receive: 00020100ffff0000
Note: In the output of show failover interface descriptor command. Two numbers are showing for each interface(inside and outside). These values are used when exchanging information regarding a particular interface, the first number in the output , sends to its peering ASA. And sending ASA expects the second number in the messages from peering ASA. These numbers are used for troubleshooting, collect the show output from both units and verify that the numbers match.
ciscoasa# sh failover
Failover On
Failover unit Secondary
Failover LAN Interface: FAIL_OVER GigabitEthernet0/2 (up)
Reconnect timeout 0:00:00
Unit Poll frequency 1 seconds, holdtime 15 seconds
Interface Poll frequency 5 seconds, holdtime 25 seconds
Interface Policy 1
Monitored Interfaces 2 of 61 maximum
MAC Address Move Notification Interval not set
Version: Ours 9.4(1)205, Mate 9.4(1)205
Last Failover at: 13:02:14 UTC Feb 9 2020
This host: Secondary – Active
Active time: 2667 (sec)
slot 0: empty
Interface outside (30.30.30.254): Normal (Waiting)
Interface inside (20.20.20.254): Normal (Monitored)
Other host: Primary – Failed
Active time: 2945 (sec)
Interface outside (30.30.30.253): Failed (Waiting)
Interface inside (20.20.20.253): Normal (Monitored)
Stateful Failover Logical Update Statistics
Link : FAIL_OVER GigabitEthernet0/2 (up)
Stateful Obj xmit xerr rcv rerr
General 768 0 757 1
sys cmd 689 0 689 0
up time 0 0 0 0
RPC services 0 0 0 0
TCP conn 0 0 0 0
UDP conn 0 0 0 0
ARP tbl 80 0 68 0
Xlate_Timeout 0 0 0 0
IPv6 ND tbl 0 0 0 0
VPN IKEv1 SA 0 0 0 0
VPN IKEv1 P2 0 0 0 0
VPN IKEv2 SA 0 0 0 0
VPN IKEv2 P2 0 0 0 0
VPN CTCP upd 0 0 0 0
VPN SDI upd 0 0 0 0
VPN DHCP upd 0 0 0 0
SIP Session 0 0 0 0
SIP Tx 0 0 0 0
SIP Pinhole 0 0 0 0
Route Session 0 0 0 1
Router ID 0 0 0 0
User-Identity 0 0 1 0
CTS SGTNAME 0 0 0 0
CTS PAC 0 0 0 0
TrustSec-SXP 0 0 0 0
IPv6 Route 0 0 0 0
STS Table 0 0 0 0
Logical Update Queue Information
Cur Max Total
Recv Q: 0 17 2195
Xmit Q: 0 1 2218
NOTE: We can see which device is active and which one is standby in the output of ‘show failover states’ command but if we want to see what kind of stateful information is being exchanged like telnet,ssh, TCP etc. this information can be check using ‘sh failover’ command. if we are able to see the connections that means failover is stateful.
Thanks For Reading………………For more on ASA topic please visit in ASA section , choose it from main menu.
detailed but good
it was long but informative
Hi there, I found your site via Google while looking for a related topic, your website came up, it looks good. I have bookmarked it in my google bookmarks.
Thanks