Source guard is a filtering feature that permits the traffic, only when source Ip address and source MAC address is matching in DHCP snooping binding table or when matching with the static source entry. below is the example of both nexus source guard and IOS IP verify unicast source
It checks the every single packet and its IP address & MAC address. If source IP address and MAC address is matching then packet will be forward for further processing. Otherwise packet will be drop. It is helpful for prevent the snoofing attack.
We can configure it on layer 2 interfaces which are entrusted DHCP snooping ports. It can also support both access and trunk ports.
Below is the example of enabling source guard on a interface:
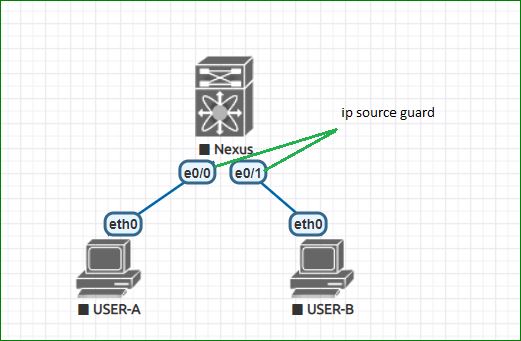
conf t
interface e1/1
ip verify source dhcp-snooping-vlanCommand to configure the static source entry:
conf t
ip source binding 1.1.1.1 0001:1234:ABCD vlan 11 interface ethernet 1/1When we are initially configuring the IP source guard. In this case, all the inbound IP traffic on that interface will be block, except the DHCP packets and packets which having a static IP source entry. It happens for a moment. once the synchronization completed , it will work fine.
Similar feature (For IOS devices):
We are also having a similar kind of feature for IOS devices. Using this feature, We can make the condition for unicast source traffic.
For example, We can configure it on a router interface with the condition like: receiving packets will be allow for further processing only when unicast source is reachable from receiving interface.
We can also use standard / extended ACLs or local interface for source reachability. Packed will only be allow for processing If condition is matching. otherwise packet will be drop.
Example:
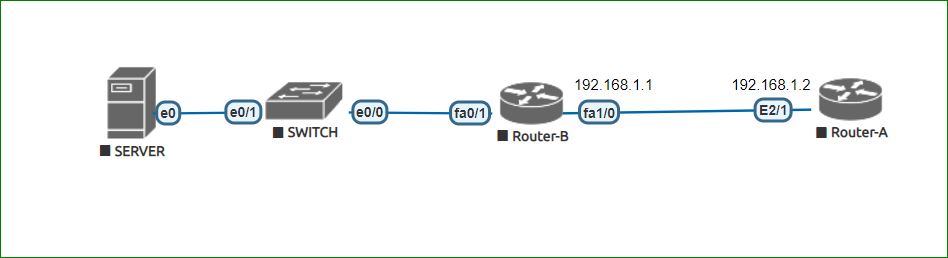
Router-A# conf t
Router-A(config)# int e2/1
Router(config-if)# ip verify unicast source reachable-via rxIn above example, We have configured the interface e2/1 on Router-A. Now router-A will allow the traffic on its interface e2/1, only when source address (192.168.1.1) is reachable from its interface e2/1. We can check it by pinging from router-A as ping 192.168.1.1 source e2/1. If it is pinging then only traffic will be allow. We are also having other options for the same command.
Commands:
Router-A# conf t
Router-A(config)# int e2/1
Router(config-if)# ip verify unicast source reachable-via rx
or
Router-A# conf t
Router-A(config)# int e2/1
Router(config-if)# ip verify unicast source reachable-via rx 10
Here, 10 is the ACL number
or
Router-A# conf t
Router-A(config)# int e2/1
Router(config-if)# ip verify reverse-path allow-self-ping 10
Here, 10 is the ACL numberKeywords:
rx :- rx means, packet will be allow only when source is reachable via interface on which packet was received. we can also use an ACL with it.
any :- If source is reachable via any interface.
allow-self-ping :- Allow router to ping itself.
….. Nexus Source Guard And IOS IP Verify Unicast Source …..
Thanks For Reading …………………
We will recommend you to read below posts: