VPC Self Isolation
VPC Self isolation is used for handle the failure. It works like the object tracking. If a module fails on primary switch then primary switch sends a message over keepalive link to inform peering (secondary switch). This message is used to inform secondary switch that one module has been failed on primary switch and now primary switch is isolating itself from network.
Secondary switch will take the primary role, after receive this message.
This is also useful when we are having mis-configuration on peer-link. Suppose, Primary switch didn’t find VLANs on its peer-link, in this case primary switch will isolate itself.
By default, self isolation is disable. We can enable it using peer-gateway and self isolation commands under VPC domain.
When we are configuring self isolation. we should make sure that we are configuring it at both switches.
While switch is isolate. We can reload , debug and remove the switch from network. But it will not affect the VPC forwarding.
we should also remember that this the isolation only for VPC. So other services will be impact . Ff we are reloading the switch or removing from network then traffic will be impact of orphan ports.
Configuring VPC Self Isolation :
vpc domain 5
peer-gateway
self-isolationManual VPC Isolation
Sometime, We require to isolate the switch. We can manually isolate the VPC by entering the shut down command under the VPC domain and we can recover it by entering no shut command.
Manually Isolating the VPC
vpc domain 5
shutdown
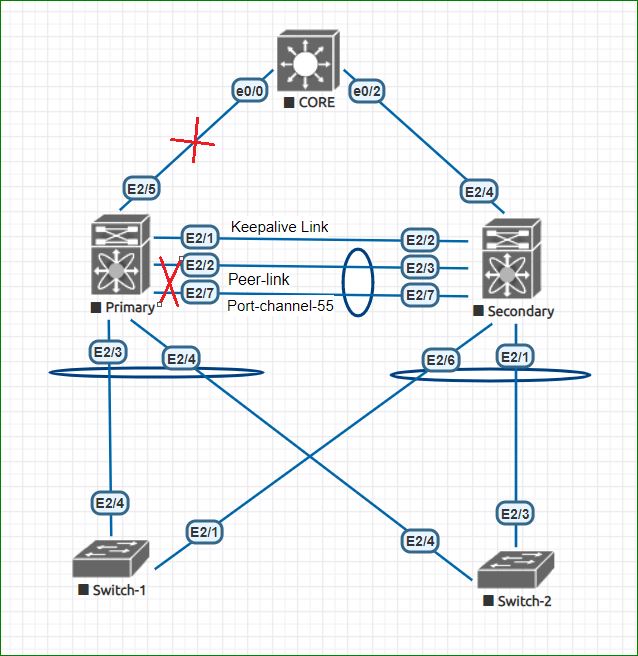
Below is the image of cisco nexus VPC Self-Isolation example. in which , Primary switch facing the network issue. it got down all up links as well as all physical links of peer link. this type of failure can we easily occur if if we are having all these links on same line card. so we should avoid the use of all important links on same module.
Thanks For Reading ………………….
We will recommend you to read below posts:
I observed that you are not posting new post from last few weeks