Private VLANs are used to add more security and to isolate the traffic of hosts into the same VLAN. when we need to separate /restrict the traffic inside a VLAN. Means we can break a broadcast network (VLAN) into multiple smaller VLANs. so users of the same VLAN can’t communicate to other users.
It is generally used at ISP end to save the VLAN numbers and separate the customers. you can also see it into data centers.
For example: An ISP provides the broadband connections and it having “n” number of customers. in this case if ISP will assign a separate VLAN to every customers then there will be a issue of VLAN numbers because we are having a limited range of VLANs (1-4094). So ISP assigns all switch ports to isolated VLAN under the same VLAN which are connected to customers and assigns the trunk port as an precocious port.
Private VLAN is also called secondary VLAN. Primary VLAN contains secondary VLANs and promiscuous port. Secondary VLAN has two types: Secondary Community VLAN and Secondary Isolated VLAN. Any port of any private VLAN can communicate With promiscuous port. Communication between private VLANs is described below. You can understand the private VLAN tree in below diagram:
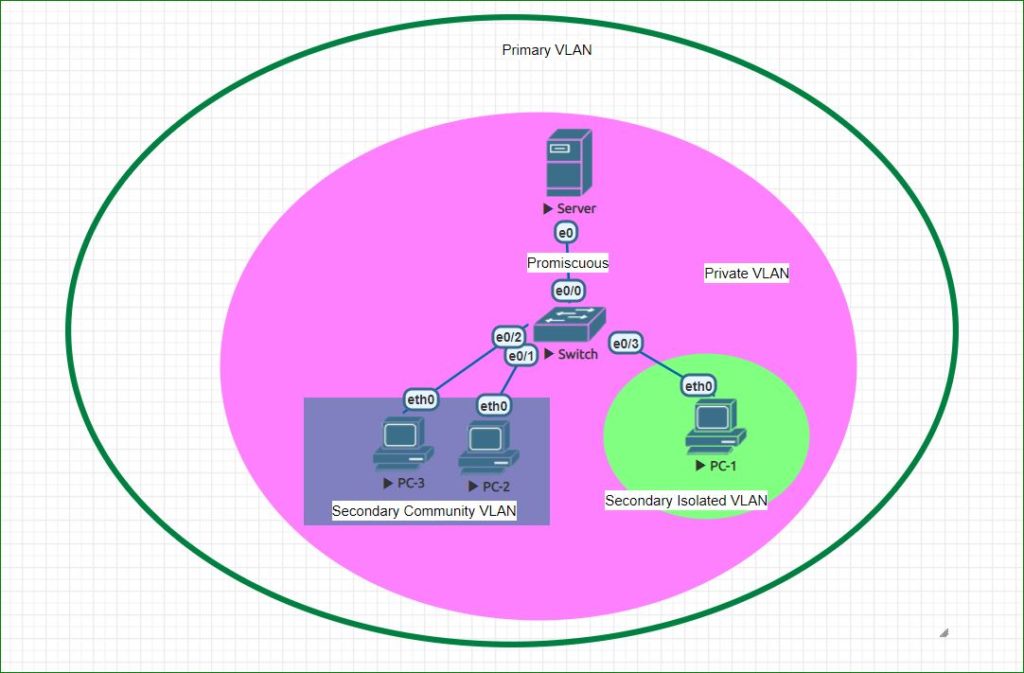
Community VLAN
With community VLAn , Each port can communicate with every port of same community VLAN as well as with promiscuous port. But communication with ports of other community VLAN is not allowed as well as communicate is not allowed between community VLAN and isolated VLAN ports.
Below is the community VLAN configuration example using above topology diagram:
Switch# conf t
Switch(config)#vtp mode transparent
Switch(config)#vlan 501
Switch(config-vlan)#private-vlan community
Switch(config-vlan)#vlan 500
Switch(config-vlan)#private-vlan primary
Switch(config-vlan)#private-vlan association add 501
Switch(config)#interface range Ethernet0/1-2
Switch(config-if-range)#switchport mode private-vlan host
Switch(config-if-range)#switchport private-vlan host-association 500 501
Switch(config)#interface Ethernet0/0
Switch(config-if)#switchport private-vlan promiscuous
Switch(config-if)#switchport private-vlan mapping 500 501
Isolated VLAN
With isolated VLAN , Each port can communicate only with promiscuous port. But ports of isolated VLAN can’t communicate with other ports of same VLAN and community VLAN ports.
Below is the isolated VLAN configuration example using above topology diagram:
Switch# conf t
Switch(config)#vtp mode transparent
Switch(config)#vlan 502
Switch(config-vlan)#private-vlan isolated
Switch(config-vlan)#vlan 500
Switch(config-vlan)#private-vlan primary
Switch(config-vlan)#private-vlan association add 502
Switch(config)#interface Ethernet0/3
Switch(config-if)#switchport mode private-vlan host
Switch(config-if)#switchport private-vlan host-association 500 502
Switch(config)#interface Ethernet0/0
Switch(config-if)#switchport private-vlan promiscuous
Switch(config-if)#switchport private-vlan mapping 500 502
Show commands:
Switch#show interface e0/1 switchport
Switch#show interface e0/1 switchport | in host-as
Switch#show vlan private vlan
Switch#show vlan private-vlan typeImportant
- When we are configuring private VLAN and also want to use the VTP then switch should be in VTP transparent mode. because VTP don’t support the private VLAN. so private VLAN configuration can’t be synchronize over trunk ports (802.1q) between switches.
- Private VLAN traffic can be pass over trunk ports but still we need to manually configure the private VLANs.
- Above both points are valid when you are using VTP version 2. But if you are using VTP version 3 then there is no restrictions. because VTP version 3 supports the private VLANs and can synchronize the private VLAN configurations.
- Private VLAn is not supported on Cisco switches below 3560 models.
“You can also use SVI (VLAN) as an Promiscuous port when you are using SVI as gateway.”
Switch# conf t
Switch(config)# interface vlan 100
Switch(config-if)# private-vlan mapping 100-103 , 199
Switch(config-if)# ip address 10.10.10.1 255.255.255.0Advance example:
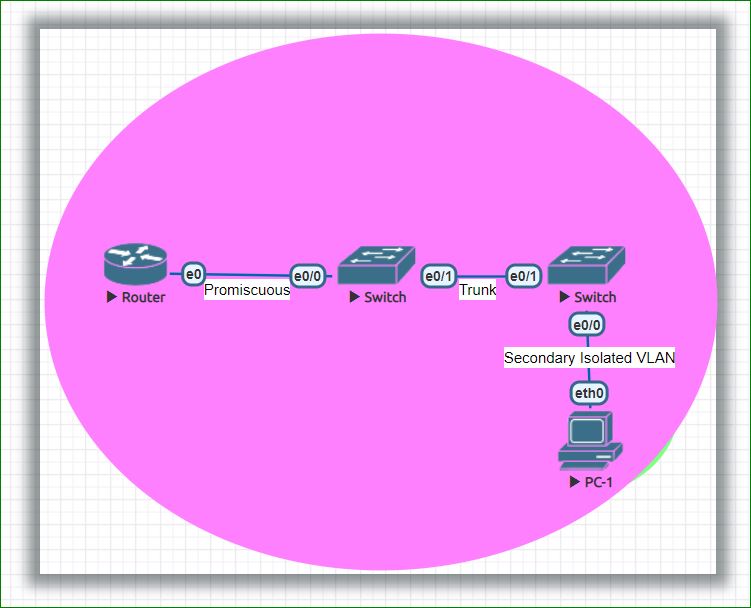
In above topology, PC-1 is connected to switch A and switch A is connected to switch B and switch B is connected to router using promiscuous port.
What will happen if PC-1 sends a packet to a destination which is not local on LAN. In this case , switch A will receive the frame from PC-1 and will forward it out to the trunk port without change its VLAN. Now switch B will receive this frame on its trunk port and will forward to its promiscuous port and once frame received on promiscuous port , Switch B will change its VLAN with primary VLAN ID.
Thanks For reading…………………………….
I will suggest you to read the below post on switch port protected:
Please complete the below online tests:
informative