ICMP Inspection
By default, ASA not inspect the ICMP packets. These are small packets and initiates for a short time. But we can enable it using below commands. if it is required.
Conf t
policy-map global_policy
class inspection_default
inspect ICMP
Allowing ICMP/PING (Outside to inside)
By default, ASA don’t allow the traffic from outside to inside (low security level to high security level. If we want to allow specific traffic from outside to inside then it can also be possible but we need to create an ACL for it.
In our case , We are allowing ping from outside to inside. So network team can check the reachability from router 2 to router 1.
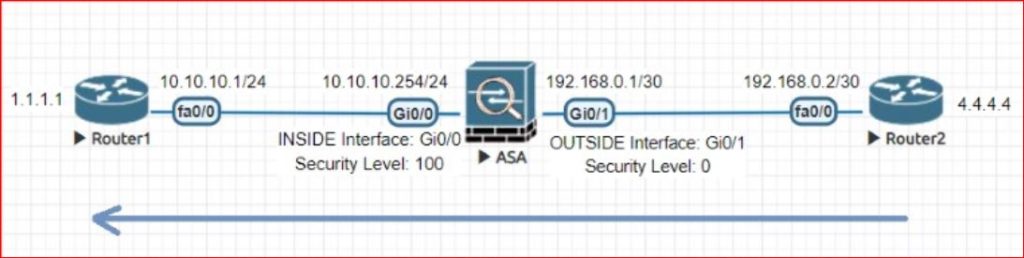
ciscoasa(config)# access-list PING extended permit icmp any host 1.1.1.1
ciscoasa(config)# access-group PING in interface outside
NOTE: when we are removing the ACL and user is accessing the application which was allowed in ACL. Then access will be continue for that user till the session is not expiring or terminating or till we are not removing the entry from connection table.