DHCP snooping acts like a firewall between DHCP servers and un-trusted host/ports. It validates the DHCP messages received from un-trusted ports and filter out the invalid messages.
Un-trusted ports are all host ports in a VLAN. which is configure for DHCP snooping.
Trusted ports are ports connected to router, switch and server.
DHCP snooping creates and maintains the DHCP snooping binding table. This table is used used to validate the DHCP messages as well as to validate the source guard.
Example:
A user can connect a device on switch port which is DHCP enabled like wifi router or any other DHCP enabled device. in this case, This rouge DHCP server device can reply to DHCP requests and assign the IP address. User who is getting the IP address from this rouge DHCP server, will be no more connected in to company network. Because this type of device assigns the IP addresses like 192.168.0.1 that will be different from company’s network. suppose, IF company is using the same series then also a problem.
It is used to prevent the rouge DHCP servers from being assign the IP addresses to users.
DHCP snooping database:
This database contains the information of un-trusted host ports like leased IP address , MAC address , lease time , binding type and interface information. But this database does’t contain the enteries of trusted ports and passes the messages directly without any check.
Database updates when device receives a message like, DHCP Ack. device removes a entry from data base when DHCP lease expires or when DHCP RELEASE message receives from a host.
Device will only validate the message or check in DHCP snooping database when host port is associated with a VLAN that is DHCP snooping enabled.
If all parameters are matching then message will be forward to DHCP server. otherwise message will be drop.
Message will be drop, If any below condition is matching:
- DHCP ACK, DHCP NAK, or DHCP OFFER is receiving on un-trusted port.
- If receiving DHCP packet including a different address then 0.0.0.0
- If a DHCP RELEASE or DHCP DECLINE message is receiving from a untrusted port and we are having an entry for it into database. But interface information is not matching with receiving interface.
- If a DHCP packet receives on untrusted interface. But source MAC address is not matching with source machine. This check is only performed, IF DHCP snooping MAC address verification is enabled.
DHCP Relay Agent:
This feature is useful, When client and DHCP server both are not on the same subnet. It forwards the DHCP packets between clients and servers. Relay agent forwarding is different from normal forwarding of an IP router.
Actually, Relay agent receives the DHCP message from client and adds the gateway address and option 82 in packet and then forwards it to DHCP server. If packet is receiving from DHCP server then relay agent removes the option 82 and forwards it to client.
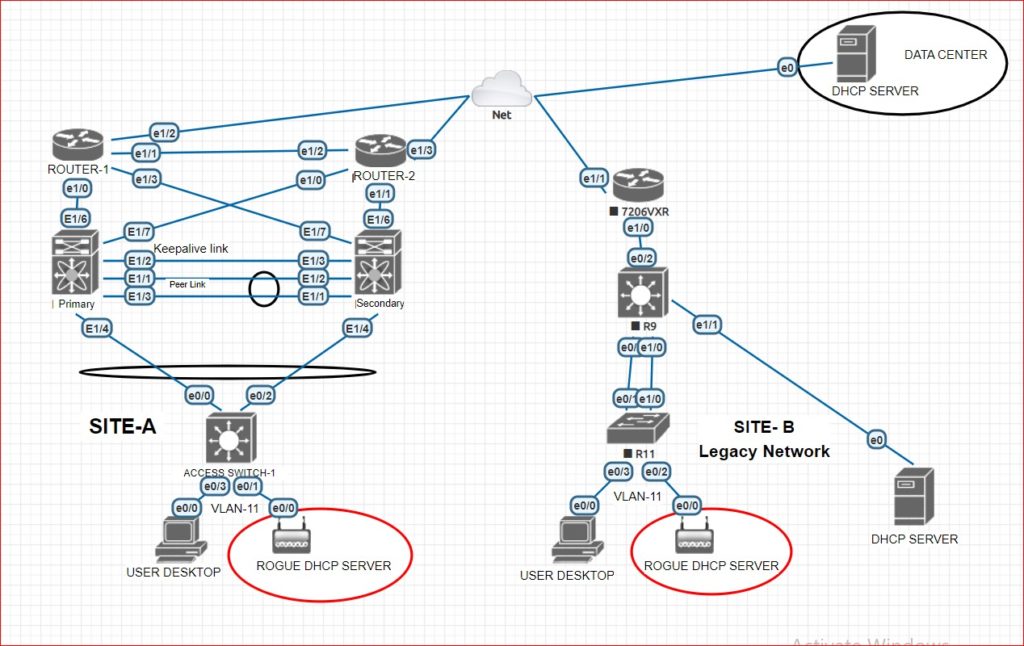
Below is the image of DHCP snooping with rogue server:
Thanks For Reading …………………
We will recommend you to read the below posts: